Beyond the Click Rate: Why Foundations Matter More Than Phishing Simulations
Added at 01/24/2026
Stop focusing on phishing click rates. Learn why foundational IT security training and understanding how the internet works is the key to long-term corporate security. Why you should give your team the time to actually learn and not just be masters of "Check-the-Box".

The Metric Trap: Training vs. Testing
In many corporate environments, "Security Awareness" has become synonymous with "Phishing Simulations". Managers stare at dashboards, obsessing over click rates. While these metrics provide a snapshot of vulnerability, they don't reflect actual knowledge. We are training employees to recognize one specific email, but we aren't teaching them how to think or technical basics and fundamentals.
If we want a resilient "Human Firewall," we need to move away from mindless microlearning and toward foundational understanding. To truly secure the enterprise, we must allow employees the time to understand the why behind the what.
Back to Basics: How the Internet Actually Works
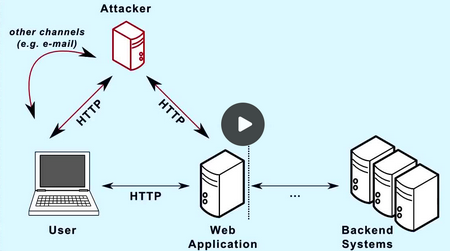
Most employees use the internet every day without truly understanding its architecture or basic technical issues. This ignorance is exactly what attackers exploit. At its core, the internet is an open-source, trust-based system. For instance:
- Anyone can own a piece of it: Attackers can buy domains that look like yours, copy your HTML/CSS in seconds, and host a perfect replica of your login page.
- The Cloud isn't magic: It's just "someone else's computer." Understanding the shared responsibility model is the first step in protecting data.
- The "Bad Guys" are Entrepreneurs: They aren't always geniuses in hoodies; they are often business-minded individuals using simple, automated technologies to trick thousands of people simultaneously.
Be aware: "Security is not a product you buy, but a process you follow." (Coined by security expert Bruce Schneier)
Understanding the Basics and the Attacker's Logic
To recognize a scam, you have to understand the basic technical scheme of the Internet. Most cyberattacks follow a predictable pattern and goal.
When employees understand that attackers leverage urgency, curiosity, and authority, they stop looking for "suspicious emails" and start identifying "suspicious psychological triggers". This mindset shift works in the office, at the client's site, and in the home office.
Beyond Phishing: The Modern Threat Landscape
A deep-dive training should cover the technical nuances that microlearning often skips. Just a few examples:
- E-Mail Security: It's not just about the sender's name. It's about headers, hidden links, and the "Reply-To" trap.
- HTTPS: What does it even mean? What does it not mean?
- The Cookie Mystery: Are cookies bad? Or Malware?
- "Hacking" the Physical World: From disposing of old hardware to the "better operating system" myth - every device, whether it's a Tablet, Mac, PC, or an IoT printer, is a potential entry point.
- Quishing (QR Code Phishing): A growing threat. Why you should never blindly scan a QR code in a public place or an unexpected email.
Conclusion: Invest in Time, Reap the Resilience

True security awareness isn't a 2-minute video you watch while drinking coffee. It's about empowering your technical project leaders, developers, and office staff with the knowledge of how the digital world functions.
Self-paced online training is excellent, but it must be comprehensive. Give your employees the time to learn the basics. When they understand the background, they don't just avoid clicking a link - they become a proactive part of your security team.
While general training for all employees is essential, (technical) project managers and developers need additional in-depth training. Managers need to understand what they have to bring to the table when it comes to their responsibility in project realization and management considering the requirements of security. This is especially true for general managers. The CEO and middle management must take the lead in establishing and modeling the security culture. When it comes to software development, alongside a security process (initiated by technical management), it is essential that the fundamental principles are learned and applied correctly.
While technical rules (like using a Password Manager) are vital, practical behavioral guidelines are the real shield. Long-term learning means internalizing these habits. Then, additional repeated microlearning can be a great tool!
HissenIT SCORM-based security awareness training for all employees (pay-once)
HissenIT - with over 20 years of experience in IT security and awareness training (onsite and online) - offers SCORM-based security training material for employees. Looking to implement a foundational security curriculum in your LMS? Whether you use SAP SuccessFactors, Moodle Workplace, or Cornerstone, we can help you deploy SCORM-compliant content that actually sticks.
- General Employees: Security Awareness and Knowledge for everyone
- General Managers and Project Managers: How to setup security processes within projects and companies in general
- Web Developers: Secure Programming of Web and Cloud Applications
HissenIT is a content creator & vendor which means - even for large enterprises - there is no vendor risk involved. The content is independent (offline) from its vendor and runs in every LMS. Moreover, HissenIT does not believe in subscription-based licenses. We believe in partnership based on results, we provide material that you want. Hence, all our course packages are pay-once lifetime licenses.
We also work with you on customization. For instance, new chapters like ready-made explanation videos on how to use your in-house login solutions or other processes.
Some courses - like for mangers and developers - include additional learning material like eBooks which is automatically included in the corresponding license. This provides an additional and easy way to lookup learning content later on.