The Human Firewall: Why smart Organizations invest in tailored Security Training with the power of the LMS
Added at 01/15/2026
In today’s digital age, the most sophisticated defense systems are often circumvented by the simplest oversight: Human error. Some stats say over 80% of security breaches are linked to mistakes like clicking a malicious link, using a weak password, or mishandling sensitive data. Technology alone cannot solve this problem.

This is where targeted Security Awareness Training (SAT) and Specialized Security Training (SST) - particularly for technical roles like developers and project managers - become the most critical component of an organization's defense strategy. By leveraging the advanced tools of a modern Learning Management System (LMS), companies can build an impenetrable "Human Firewall", meeting compliance requirements like ISO 27001 while genuinely enhancing cyber resilience.
Here is a deep dive into why these trainings are essential and how to use LMS features to deliver them effectively.
The Strategic Value of the Human Firewall
Security training is no longer a check-the-box exercise; it is an investment that yields measurable returns across three key dimensions: Risk Reduction, Compliance, and Culture.
1. Measurable Risk Reduction: Reducing Human Error
General SAT aims to instill the "security mindset" in all employees, regardless of role.
- Phishing and Social Engineering: Regular, high-quality training teaches employees to recognize and report suspicious activity across multiple channels (email, SMS, even voice). Tracking phishing simulation click rates is a crucial metric, and effective training programs have been shown to drastically reduce this rate over time.
- Data Handling: Employees learn crucial best practices for handling sensitive data - from using strong, unique passwords to adhering to the Clean Desk Policy. This directly reduces the likelihood of insider threats, whether malicious or accidental.
- Tangible ROI: Studies consistently show a substantial Return on Investment (ROI) for security awareness programs, often exceeding a 7-fold return by preventing a single, costly breach.
2. Meeting and Exceeding Compliance Requirements (e.g., ISO 27001)
For organizations seeking or maintaining certification under standards like ISO/IEC 27001, robust training is mandatory, not optional.
- Audit-Ready Proof: Control A.8.2.2 (Information Security Awareness, Education, and Training) requires definitive proof of competency. The LMS provides the Audit Trail needed: detailed reports showing who completed which course, when, and with what score. This automated documentation is indispensable for passing external audits quickly and reliably.
- Global Standardization: Using a centralized LMS ensures that every employee, regardless of location or language, receives the same, consistent security messaging, simplifying compliance across global operations.
3. Cultivating a Proactive Security Culture
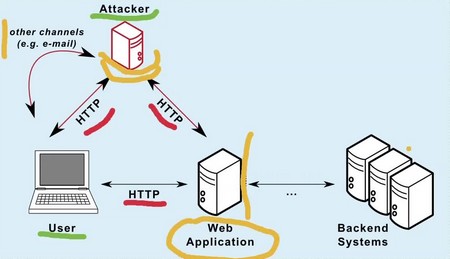
Effective training transforms security from a niche IT topic into a shared organizational value.
- Empowerment: When employees understand why security matters (both personally and professionally), they become an active part of the defense. They are empowered to flag risks and are rewarded for proactive behavior.
- Minimizing Damage: In the event of an incident (a suspected malware infection or ransomware), a well-trained workforce knows how to react quickly - often minimizing the damage and aiding the incident response team.
The Critical Role of Specialized Security Training (SST)
While general awareness is for everyone, highly technical and strategic roles require deep, specialized knowledge. Two groups stand out: Technical Project Managers and Software Developers.
1. Security Training for Technical Project Managers
Project Managers (PMs) - but also General Managers, CEOs, CISOs etc. (everything starts from the top) - are the bridge between strategy, development, and risk. Equipping them with cyber-risk literacy is crucial.
- Holistic Risk Management: Training allows PMs to integrate cyber risk into their core risk management framework. They learn to identify potential security vulnerabilities during project planning, not just at the end.
- Secure by Design: PMs with security knowledge can effectively enforce the "Security by Design" principle. They ask the right questions during vendor selection, technology choices, and sprint planning, ensuring security requirements are met from the inception of a project.
- Communication Bridge: A PM who understands terms like "zero-day vulnerability," "threat modeling," or "supply chain attack" can communicate more effectively with the security team, leading to smoother project execution and faster issue resolution.
2. Security Training for Developers (Secure Programming)
For developers, security training is not about awareness, but about competency and skill application. This training focuses on Secure Programming principles to eliminate vulnerabilities in the code itself.
- OWASP Top 10 Focus: Courses are typically focused on preventing real-world threats listed in the OWASP Top 10 (Code Injections, XSS, Broken Access Control, etc.).
- Vulnerability Remediation: Developers learn common coding pitfalls and how to write inherently secure code, saving enormous time and cost later in the product lifecycle (it is far more expensive to fix a vulnerability in production than during the development phase).
- Language-Specific Training: Training must be tailored to the technologies used (e.g., Java, JavaScript, Python, C++). This ensures relevance, engagement, and immediate applicability in their daily work.
Leveraging LMS Tools for Maximum Security Impact
A modern LMS - whether it is an Enterprise solution like SuccessFactors Learning, Cornerstone, TalentLMS etc. or an open-source system like Moodle Workplace - provides the architecture to deliver, track, and enforce all these training types strategically.
1. Dynamic Rules & Automation
The LMS automatically enrolls all staff into according training material. Role-based assignments are possible including tracking success to fulfill audit requirements.
2. Independence & Content Standards (SCORM/xAPI)

The LMS, all its users and audit-relevant data is completely managed by the enterprise itself. The training material can be obtained from specialized content vendors.
3. Monitoring, Dashboards & Reporting
The LMS provides real-time visibility for the CISO or responsible Security Officer. Again, an easy way to manage and track provable awareness training results for various employee groups. This helps to improve the actual "Human Firewall" and eases security process auditing.
Conclusion: Security as a Continuous Process
The threat landscape is constantly changing, meaning security training cannot be a one-time event. It must be a continuous, evolving process supported by robust LMS architecture.
By moving beyond simple "awareness" and implementing targeted, role-specific Secure Programming and Technical Project Management training, organizations transform their security posture from reactive to proactive. They use the LMS not just as a delivery system, but as the engine of compliance, competency tracking, and organizational resilience.
Investing in the human element, powered by the right technology, is the most cost-effective way to protect assets, satisfy global regulations, and build a competitive advantage in the digital economy.
Scalability
A SCORM course can be completed simultaneously by 100 or 100,000 employees worldwide without requiring an instructor. This is a crucial advantage for global organizations, allowing for rapid, uniform deployment of mandatory training (e.g., annual security awareness) across all jurisdictions.
Actionability & Real-Time Intervention
The IT Security Officer can use the LMS to see in real-time which employees have missed the deadline. They can then target these individuals specifically with email reminders or, hypothetically, restrict their system access until compliance is achieved. This functionality is essential for enforcing mandatory training requirements efficiently
HissenIT SCORM-based security awareness training for all employees (pay-once)
HissenIT - with over 20 years of experience in IT security and awareness training (onsite and online) - offers SCORM-based security training material for employees:
- General Employees: Security Awareness and Knowledge for everyone
- General Managers and Project Managers: How to setup security processes within projects and companies in general
- Web Developers: Secure Programming of Web and Cloud Applications
HissenIT is a content creator & vendor which means - even for large enterprises - there is no vendor risk involved. The content is independent (offline) from its vendor and runs in every LMS. Moreover, HissenIT does not believe in subscription-based licenses. We believe in partnership based on results, we provide material that you want. Hence, all our course packages are pay-once lifetime licenses.
We also work with you on customization. For instance, new chapters like ready-made explanation videos on how to use your in-house login solutions or other processes.
Some courses – like for mangers and developers – include additional learning material like eBooks which is automatically included in the corresponding license. This provides an additional and easy way to lookup learning content later on.