Introducing cloaked (headerless) files - CrococryptFile 1.3 released
Today, we released CrococryptFile 1.3 as free download. This version includes a new crypto suite: "cloaked" archives. This kind of suite encrypts archives without headers. What this exactly means, we explain in the following.
CrococryptFile v1.3 includes the crypto suite "cloaked archives". What exactly does "cloaked" mean in this case? The answer is related to the topic of "plausible deniability", a feature for instance of the famous TrueCrypt and similar tools. However, there is no real deniability using single files.
Basics
TrueCrypt - as an example - allows to store an encrypted container within an encrypted container. Since without knowing the decryption key an encrypted container looks like random numbers, a hidden container within an encrypted container is generally not detectable. I am solely talking about technical detection. It has been discussed very often which use plausible deniability can have in practice, let's say in case of torture, but that is not the topic of this article.
A "cloaked" CrococryptFile archive also looks like a file of random numbers. The archive has no visible header if you do not have the corresponding decryption key. However, a file full of random numbers can be detected as such and hence can be identified as an encrypted file with a very high probability. In this respect, there is no easy deniability in that case. On the other hand, no one can prove or verify that the file is a CrococryptFile archive.
Use case
A file without header, without file extension and maybe a meaningless filename can be used as a backup archive, for instance to put into your cloud storage. CrococryptFile works stream-based and can create and extract archives of arbitrary size very efficiently.
For the use case of cloud backups the usage of cascading ciphers in this format is also interesting. AES and Twofish using 256 bits keys are used. This is similar to the file encryption tool CrococryptMirror.
Encryption scheme
Other than for instance TrueCrypt, this archive format of CrococryptFile does not use a fixed iteration count when deriving the encryption key from the password or passphrase. The current version indeed uses a specific value between 50000 and 60000 (suitable for using on a standard PC at the moment), but this can be changed in the future or even be made customizable by the user and still would be compatible to the format. Following PBKDF2 (PKCS#5), the current implementation works with an iteration count up to 9223372036854775807 (maximum long value). Even this could be enlarged.
The correct derived keys (and hence the correct passphrase) are determined through the first 128 bytes of the file which - as said before - looks like random numbers without any pattern. The first 64 bytes are a random vector, the second 64 bytes contain the random vector encrypted using AES and Twofish. At every single iteration step, it will be checked if both values match by performing a decryption attempt. The iteration count used at generation time (encryption) is not stored.
The technically adept reader has probably already realized that the derivation is an endless loop. That means, CrococryptFile will never finish in case a wrong passphrase is provided. However, the decryption process can be canceled comfortably at any time by the user. In the normal case, the decryption lasts only a few seconds - if you know the passphrase. An attacker however who wants to try a brute-force attack using a password generator or a password list has to use a fix iteration count to make the attack reasonable.
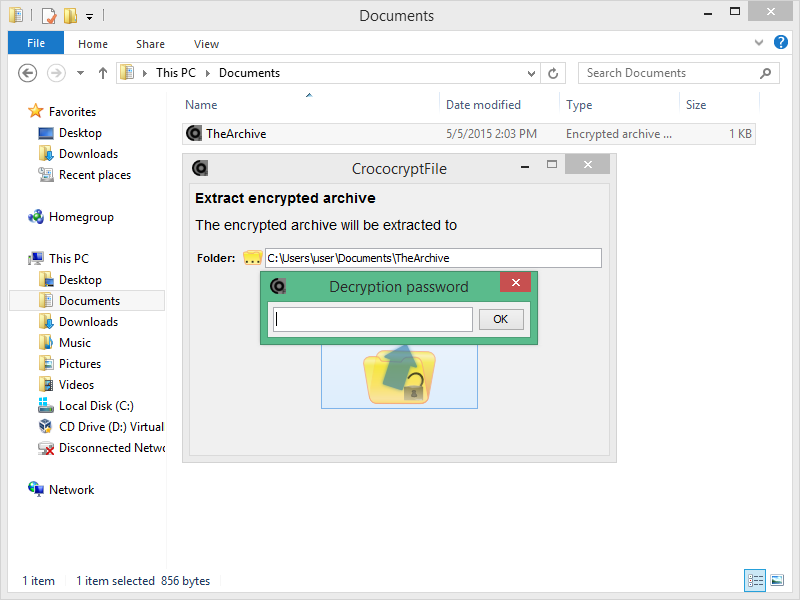
This format obviously is not meaningful for every use case. And to clarify again: CrococryptFile saves this format without file extension. The file can be renamed arbitrarily and a decryption attempt can be performed on any file using the corresponding application option (Windows: see startmenu). However: CrococryptFile itself does not know if the file is a known archive until it discovers the fitting key!
The sky is the limit
To "cloak" files even better, there exists a second mode which enlarges the created archives to a multiple of 1MB using random numbers. At decryption these will simply be ignored. It is also possible to enlarge these files to an arbitrary size using external random number generators and tools to add data at the end of the file. This data will be ignored as well when decrypting.
Further links
Downloads of different editions and more information: CrococryptFile Homepage.
Categories: News IT Security Background articles
Comments
Post your comment
Share
If you like this page, it would be a great thing if you share it with others:
reddit Digg StumbleUpon XING
WhatsApp Telegram